Cybersecurity researcher Bob Dyachenko, in collaboration with Cybernews, has unearthed a data dump of 26 billion records of what they call the “Mother of all breaches”.
The data leak contains 12 terabytes of data across 3,800 folders with each folder systematically indexing a data breach.
According to the researchers, while the leaked dataset contains mostly information from past data breaches, there is a high probability for new data as well.
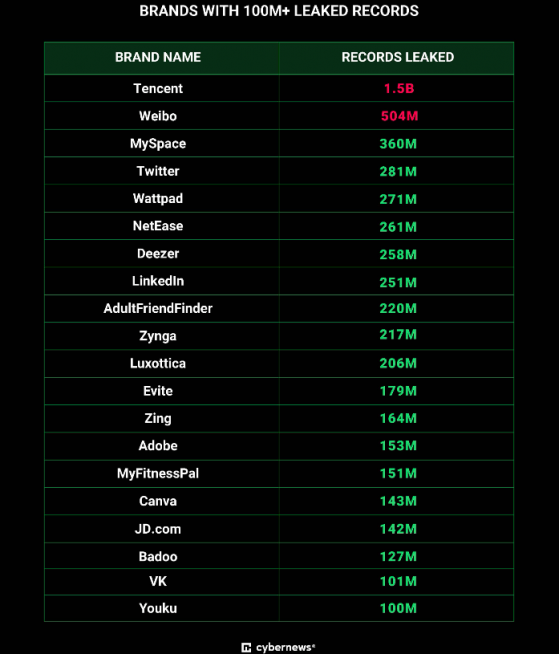
Amongst the most affected are Chinese brands Tencent and Weibo with 1.5 billion and 504 million records exposed respectively from previous leaks.
Social media giants Twitter, and LinkedIn have 200 million+ records exposed – most likely from past breaches as well.
‼️@CyberNews research team, together with #cybersecurity researcher @MayhemDayOne, have discovered billions upon billions of exposed records on an open instance whose owner is unlikely ever to be identified.⤵️#MOAB #databreach #dataleak #infosecurityhttps://t.co/3ofLNd31Fz— CyberNews (@CyberNews) January 22, 2024
“Extremely dangerous”
Researchers believe that the owner of the data dump has a vested interest in storing large amounts of data and, therefore, could be a malicious actor, data broker, or some service that works with large amounts of data.
“The dataset is extremely dangerous as threat actors could leverage the aggregated data for a wide range of attacks, including identity theft, sophisticated phishing schemes, targeted cyberattacks and unauthorized access to personal and sensitive accounts,” the researchers said.
Scale and implications
While the Cybernews data leak checker previously indexed 15 billion records from 2,500 breaches, the latest data leak surpasses the scope of all previously documented data breaches.
The implications of this breach for individual users are profound. The likelihood of duplicate records notwithstanding, the leak’s scale presents a heightened risk for credential-stuffing attacks, identity theft and sophisticated phishing schemes.
Moreover, the inclusion of data from various government organisations globally escalates the potential for targeted cyberattacks and unauthorized access to sensitive accounts.
How do I protect myself?
In response to these risks, individuals must practice rigorous cyber hygiene.
This includes the adoption of strong, unique passwords, enabling multi-factor authentication and staying alert to phishing attempts.
Additionally, individuals should monitor their accounts for any signs of unauthorised access and promptly update security settings where necessary.
Read more on Proactive Investors AU