This past Saturday, June 2, the ZenCash (ZEN) cryptocurrency experienced a 51% attack. For those unfamiliar with the term, it refers to an assault on a blockchain by a group of miners, controlling more than 50% of the network's mining hashrate, or computing power. As a result the attackers were able to double spent over $550,000 worth of the tokens.
ZEN is a fork of ZClassic which launched in May 2017 using the same codebase as ZCash. "At the time of the attack the ZEN network hash rate was 58MSol/s," revealed ZenCash in a official statement on alt-currency's website:
It is possible that the attacker has a private mining operation large enough to conduct the attack and/or supplement with rental hash power. Net hash rate is derived from the last mined block and therefore live hash rate statistics are not available.
The attack is concerning, of course. Perhaps the more appropriate concern, however, is, was the attack avoidable? The short answer: absolutely.
There are a number of steps which could have been taken and ways in which blockchain security can be improved to prevent this from happening again. Martin Wos, co-founder of Block Stocks says this is a problem that is likely to continue to occur due to so many proof-of-work (PoW) coins sharing similar hashing functions.
Attack Cost Is Cheap
There is also a new website, 51 Crypto, which outlines the estimated hourly cost of launching a so-called 51% attack on various cryptocurrencies. In particular it highlights the risk to smaller coins.
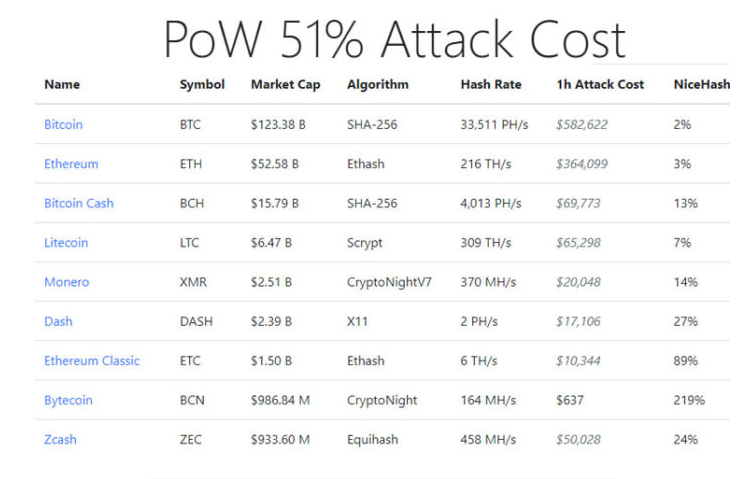
The list (an abbreviated version, above) highlights just how cheap it is to attack specific cryptocurrencies. Wos says:
Crypto 51 just published a study demonstrating just how cheap these 51% attacks can be. We expect to see other currencies circumvent this problem by utilizing different blockchain consensus mechanisms— namely PoS, dPoS, and dBFT among others. It is what has led Block Stocks to develop our own proprietary hashing algorithm known as PPoKW.
Dr. Robert Statica, of decentralized trading platform BLAKLedger and the cryptocurrency BLAKCoin, explains that the Bitcoin network and most blockchains that require coins to be mined are open and not permissioned. Is it possible, then to thwart these attacks?
For the coins that require mining, one method to defend against the 51% attack is to increase the number of confirmation, start blacklisting and blocking people/machines/accounts suspected as part of the attack, and by making changes of the protocol itself it it's time consuming and prone to errors and security flaws.
For example, when BTC-e responded to a 51% attack on “Feathercoin,” they increased their confirmation requirements to 100 blocks instead of the standard 6 blocks. But that's only a partial solution at best explains Statica. It only slows down the attack and requires more computational power to achieve majority, but it wouldn't stop a determined attacker.
Although many developers and blockchain operators claim that 51% attacks are annoying, not to mention damaging to the alt-currency under attack, they fail to acknowledge that unknown miners with huge computational power could render their chains inoperable relatively quickly, tanking coin prices. But all this could be dealt with fairly easily notes Statica. It would just require better coins with end-to-end security. It's a solution which would represent the next generation of cryptocoins.
